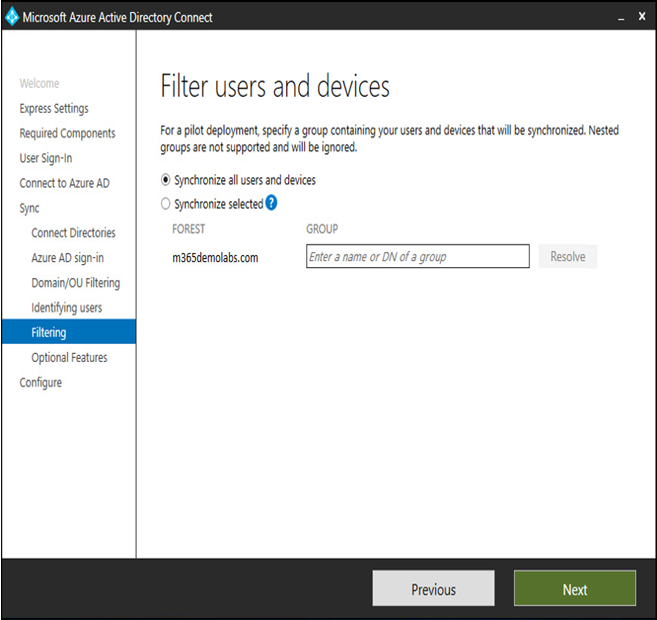
Jul 31, 2024
Managing and monitoring Microsoft 365 license allocations– Planning and Managing Azure AD Identities
If identity is the foundation for security in the Microsoft 365 platform, licensing is the entitlement engine that is used to grant identities access to the tools and applications.
Every Microsoft 365 service is tied to a license—whether that’s individual product licenses for Exchange Online or SharePoint Online or bundled offerings such as Microsoft 365 E3, which include multiple services.
In Microsoft terminology, there are a number of key terms to be aware of:
- Licensing plans: In broad terms, a licensing plan is any purchased licensing item. For example, standalone Exchange Online P2 and Microsoft 365 E3 are both examples of licensing plans.
- Services: Also known as service plans, these are the individual services that exist inside of a licensing plan. For example, Exchange Online P2 has a single Exchange Online P2 service plan, while Microsoft 365 E3 has an Exchange Online service plan, a Microsoft 365 Apps service plan, a SharePoint Online service plan, and so on.
- Licenses: This is the actual number of individual license plans of a particular type that you have purchased. For example, If you have 5 subscriptions to Exchange Online P2 and 5 subscriptions to Microsoft 365 E3, you have 10 licenses (or 5 each of Exchange Online P2 and Microsoft 365 E3). Licenses are frequently mapped 1:1 with users or service principals, though some users may have more than one license plan associated with them.
- SkuPartNumber: When reviewing licensing in PowerShell, the SkuPartNumber is the keyword that maps to a licensing plan. For example, Office 365 E3 is represented by the ENTERPRISEPACK SkuPartNumber.
- AccountSkuId: The AccountSkuId is the combination of your tenant name (such as Contoso) and the SkuPartNumber or licensing plan. For example, the Office 365 E3 licensing plan belonging to the contoso.onmicrosoft.com tenant has an AccountSkuId of contoso:ENTERPRISEPACK.
- ConsumedUnits: Consumed units represent the number of items in a licensing plan that you have assigned to users. For example, if you have assigned a Microsoft 365 E3 licensing plan to three users, you have three ConsumedUnits of the Microsoft 365 E3 licensing plan. If reviewing licensing from the Azure AD portal, this field is sometimes displayed as Assigned.
- ActiveUnits: Number of units that you have purchased for a particular licensing plan. If reviewing licensing from the Azure AD portal, this field is sometimes displayed as Total.
- WarningUnits: Number of units that you haven’t renewed purchasing for in a particular license plan. These units will be expired after the 30-day grace period. If reviewing licensing in the Azure AD portal, this field is also sometimes displayed as Expiring soon.
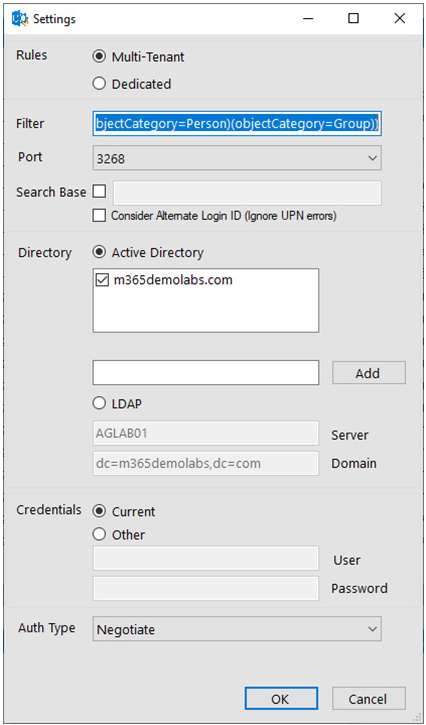
You can easily view purchased licensing plan details in the Microsoft 365 admin center under Billing | Licenses:
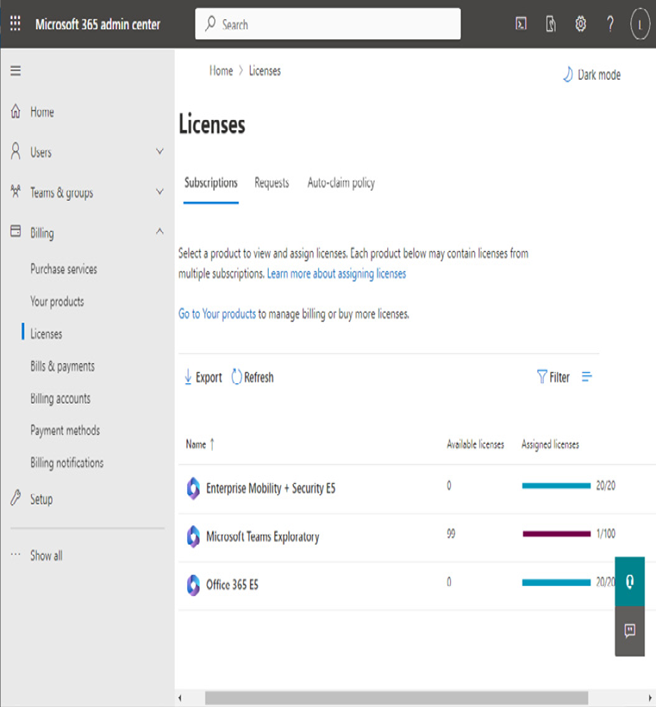
Figure 5.22 – License details in the Microsoft 365 admin center
You can assign licenses in many ways:
- Through the Licenses page in the Microsoft 365 admin center (Microsoft 365 admin center | Billing | Licenses)
- In the properties of a user on the Active users page in the Microsoft 365 admin center (Microsoft 365 admin center | Users | Active Users | User properties)
- To users through the Licenses page in the Azure AD portal (Azure AD Portal | Azure AD | Licenses | Licensed users)
- To users through the User properties page in the Azure AD portal (Azure AD Portal | Azure AD | Users | User properties)
- To groups through group-based licensing (Azure AD Portal | Azure AD | Licenses | Licensed groups)
- Through PowerShell cmdlets such as Set-MsolUserLicense
Each licensing method provides you with similar options for assigning license plans to users, including assigning multiple license plans or selectively enabling service plans inside an individual license plan.
For example, in the Microsoft 365 admin center, you can view and modify a user’s licenses on the Licenses and apps tab of their profile.
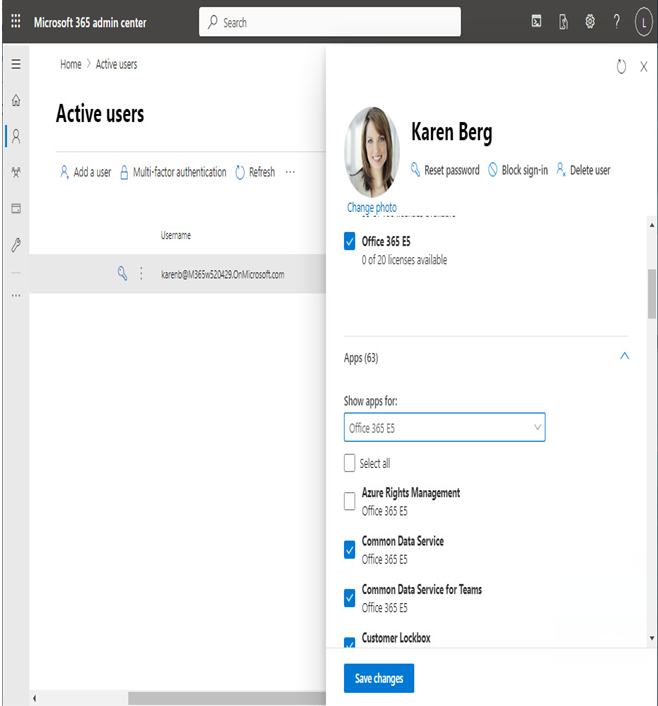
Figure 5.23 – User license management
As you can see in Figure 5.23, the user has the Office 365 E5 licensing plan enabled as well as individual services such as Common Data Service, Common Data Service for Teams, and Customer Lockbox, while the Azure Rights Management service plan for this licensing plan is disabled.
More Details