Jan 24, 2022
Understanding Azure AD Connect with multi-forest scenarios– Planning Identity Synchronization
Azure AD Connect also supports several multi-forest scenarios.
In a basic multi-forest scenario, you have one or more on-premises Active Directory forests all contributing unique objects to a single Azure AD tenant.
You might need to support a configuration like this if you have multiple business units within your organization with their own autonomous Active Directory environments that all want to share a single Microsoft 365 environment:
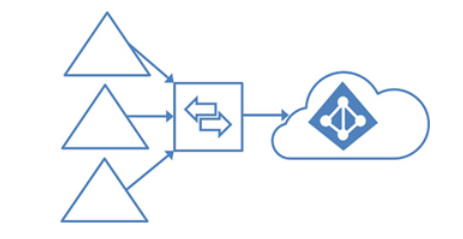
Figure 3.2 – Multiple Active Directory forests contributing to a single Azure AD tenant
There are other organizational scenarios where you may need to support multiple forests. Large organizations sometimes configure multiple directories in what’s called a resource forest configuration.
In this structure, application resources (such as Microsoft Exchange) are configured in one forest (called the resource forest). A trust relationship is established with another forest containing accounts (intuitively called the account forest). The trust allows objects from the account forest to access applications and services in the resource forest. The user objects in the account forests are linked to a corresponding security principal account in the resource forest, thereby granting access to the resource forest. See Figure 3.3:
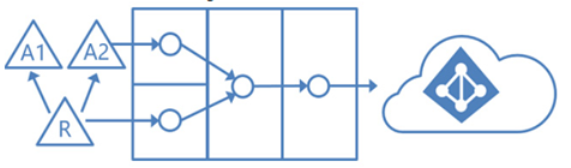
Figure 3.3 – Account forests and a resource forest contributing to a single Azure AD tenant
Another common multi-forest scenario involves two or more on-premises organizations that utilize some other form of directory synchronization (such as MIM GALSync) to ensure that each organization’s Exchange environment contains a full list of the objects in their partner’s directories. This example is shown in Figure 3.4:
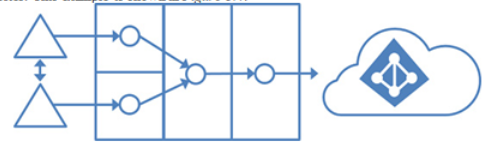
Figure 3.4 – Multiple forests with on-premises synchronization to a single Azure AD tenant
In this scenario, users have a single primary account that they use for accessing services and resources. That account is represented in the partner organization’s directory as a contact object.
Multiple forests, multiple users, multiple options
Multi-forest configurations can be quite tricky. During the Azure AD Connect setup, you’ll be prompted to select how your users are represented across the organization. You have two core options: Users are represented only once across all directories and User identities exist across multiple directories.
The first option is straightforward – it’s a scenario where users only have one object.
The second option, though, has two additional choices: to match using Mail attribute or ObjectSID and msExchangeMasterAccountSID attributes.
In an on-premises directory synchronization scenario (which Microsoft refers to as full mesh), users may be represented by several objects, such as a security principal (user account), as well as a contact object in other forests. For this scenario, you would choose to match users based on the mail attribute.
In a resource forest configuration, users typically have more than one identity: an identity in the account forest that is linked to a corresponding account in the resource forest. Typically, the account in the resource forest is set to disabled. In an Exchange resource forest scenario, the objects are linked by copying the ObjectSID value from the user object in the account forest to the msExchangeMasterAccountSID value of the user object in the resource forest. With an Exchange resource forest design, you’ll want to select the ObjectSID and msExchangeMasterAccountSID attributes option.
More Details