Nov 16, 2022
Choosing between Azure AD Connect and Azure AD Connect Cloud Sync– Planning Identity Synchronization
Azure AD Cloud Sync is the next evolution of the directory synchronization product. While it does not yet have full parity with Azure AD Connect features, Azure AD Connect Cloud Sync (sometimes referred to as Cloud Sync) can provide additional features and benefits that Azure AD Connect cannot:
- While Azure AD Connect requires on-premises connectivity between the Azure AD Connect server and all connected forests, Azure AD Connect Cloud Sync can import identities from forests that do not have site-to-site connectivity. This makes Cloud Sync advantageous when dealing with mergers and acquisitions as well as organizations that have multiple, disconnected business units.
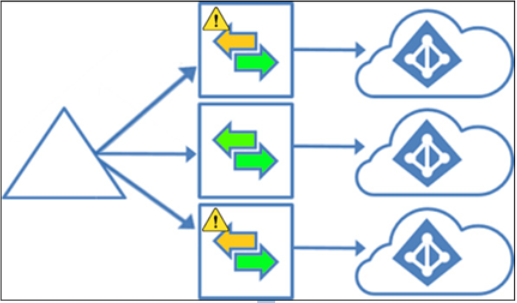
- Lightweight on-premises provisioning agents with cloud-managed sync configuration. Multiple sync agents can be installed to provide fault tolerance and redundancy for password hash synchronization customers.
However, Cloud Sync provides fewer overall features. The following list identifies the core feature gaps:
- Cloud Sync does not support on-premises LDAP directories.
- Cloud Sync does not support device objects.
- Pass-through authentication is unavailable with Cloud Sync.
- Advanced filtering and scoping (such as by using object attributes) are not supported with Cloud Sync, nor are advanced configurations of custom synchronization rules.
- Azure AD Connect Cloud Sync does not support more than 150,000 objects per AD domain, nor does it support Azure AD Domain Services (Azure AD DS). Since Cloud Sync is limited to 150,000 objects, it does not support large groups (up to 250,000 members).
- Cloud Sync does not support Exchange hybrid writeback or group writeback.
- Cloud Sync cannot merge object attributes from multiple source domains.
A full comparison of features is available at https://learn.microsoft.com/en-us/azure/active-directory/cloud-sync/what-is-cloud-sync. As you can see from the previous lists, Azure AD Connect Cloud Sync is potentially a good option for organizations that don’t have more than 150,000 objects in any single domain, don’t require object or property writeback, and don’t need to heavily customize synchronization rules.
Planning user sign-in
The final step in planning your hybrid identity solution is around what type of sign-in experience you want to deploy for your users. As discussed briefly in the Designing synchronization solutions section, there are three core methods for managing user sign-in:
- Password hash synchronization
- Pass-through authentication
- Federation
While all three of these solutions utilize some sort of identity synchronization technology, knowing the features and capabilities of each will help you choose the option that’s right for your organization.
Let’s explore each of these options in a little more detail.
More Details